The automotive industry is undergoing a seismic shift with the rise of Software-Defined Vehicles (SDVs). These vehicles rely heavily on software to deliver advanced features, enhanced performance, and improved user experiences. A key enabler of this transformation is Over-the-Air (OTA) updates, which allow manufacturers to remotely deploy software patches, bug fixes, and new features. However, as OTA updates become a standard feature, they also introduce significant cybersecurity challenges. This article explores the growing importance of OTA updates, the risks they pose, and how automakers are addressing these challenges to ensure secure and seamless updates.
The Growing Importance of OTA Updates in SDVs
OTA updates have revolutionized the way automakers maintain and improve vehicle software. Traditionally, software-related issues required physical recalls, which were costly, time-consuming, and inconvenient for vehicle owners. With OTA updates, manufacturers can address these issues remotely, reducing downtime and improving customer satisfaction. For example, Tesla has been a pioneer in leveraging OTA updates to resolve recalls. In 2024, Tesla resolved 99% of its recalls through OTA updates, minimizing the need for service center visits. This approach not only saved time and resources but also ensured that vehicles remained operational and secure. However, not all automakers have embraced OTA updates to the same extent. According to recent data, only 13% of software-related recalls across the industry are addressable via OTA updates. This highlights a significant gap in the adoption and implementation of OTA technology.
Cybersecurity Challenges in OTA Updates
While OTA updates offer numerous benefits, they also expand the attack surface for cyber threats. As vehicles become more connected, they are increasingly vulnerable to attacks that can compromise safety, privacy, and functionality.
1. Vulnerabilities in OTA Systems
OTA systems rely on complex communication protocols and software architectures, making them susceptible to various types of attacks. For instance, attackers can intercept updates, inject malicious code, or disrupt the update process. A notable example is the Spireon incident, where attackers gained administrative access to 15.5 million vehicles, allowing them to remotely control critical functions such as starting, shutting down, and updating firmware.
2. Centralized Security Risks
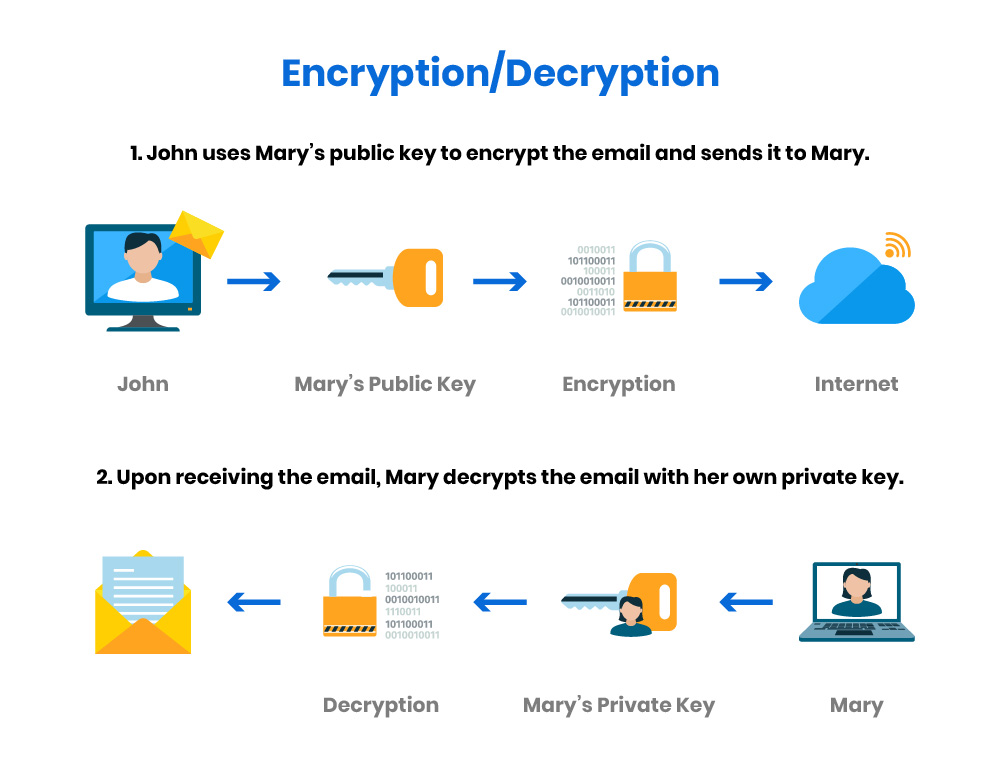
Many OTA systems use Public Key Infrastructure (PKI) for authentication and data integrity. While PKI provides a strong foundation, its centralized nature creates a single point of failure. If a Certificate Authority (CA) is compromised, attackers can issue fraudulent certificates and bypass security measures. The Lenovo Superfish incident and the DigiNotar breach are stark reminders of the risks associated with centralized PKI systems.
3. Supply Chain Vulnerabilities
The automotive supply chain is another weak point in OTA security. Third-party components, legacy systems, and external integrations can introduce vulnerabilities that attackers can exploit. For example, vulnerabilities in third-party software or hardware can provide entry points for cyberattacks, compromising the entire vehicle ecosystem. In 2020, Honda recalled 608,000 vehicles due to software bugs in third-party components that caused incorrect speedometer readings and rear-view camera malfunctions. While the issue was resolved via OTA updates, it highlighted the risks of relying on external suppliers.
Strategies for Securing OTA Updates
To address these challenges, automakers are adopting a multi-layered approach to cybersecurity, focusing on encryption, authentication, and traceability.
1. Encryption and Authentication
The Advanced Encryption Standard (AES), particularly AES-256, is widely used to encrypt OTA update packages. AES ensures that even if an attacker intercepts the update, the data remains unreadable. Public Key Infrastructure (PKI) and Transport Layer Security (TLS) are critical for verifying the legitimacy of updates. PKI uses digital signatures to authenticate the source of updates, while TLS encrypts the communication channel between the vehicle and the update server. Additionally, secure bootloaders are employed to verify the integrity of the software during the boot process. If the software has been tampered with, the bootloader halts the process, preventing malicious code from executing

2. Decentralized Security Solutions
DLT, such as blockchain, provides a decentralized and tamper-proof ledger for recording OTA updates. For example, IOTA’s Tangle network is being used to store hash values of firmware updates, ensuring data integrity and transparency. This approach eliminates the risks associated with centralized certificate authorities (CAs). DIDs enable vehicles to have unique, self-sovereign identities that are not reliant on centralized authorities. Combined with Verifiable Credentials (VCs), DIDs ensure that updates are securely authenticated and traceable.
3. Traceability and Compliance
End-to-End Visibility: Automakers are implementing solutions that provide end-to-end visibility into the update process, from the cloud to individual Electronic Control Units (ECUs). For example, UNECE Regulation R156 mandates that manufacturers maintain detailed records of software updates, including version history and compliance checks
In Conclusion
OTA updates are a game-changer for the automotive industry, enabling manufacturers to deliver new features and address software issues remotely. However, the increasing reliance on OTA technology also introduces significant cybersecurity challenges. Automakers must adopt a multi-layered approach to security, leveraging encryption, decentralized technologies, and traceability to ensure seamless and secure updates. As the industry continues to evolve, collaboration between automakers, technology providers, and regulators will be essential to address these challenges and unlock the full potential of SDVs. By prioritizing cybersecurity and innovation, the automotive industry can drive the future of mobility while ensuring safety, privacy, and trust.

 日本語
日本語 한국어
한국어 Tiếng Việt
Tiếng Việt 简体中文
简体中文